Automotive Cybersecurity
Automotive Cybersecurity Services

What we offer:
- Automotive cybersecurity consulting services
- Cybersecurity for software-defined vehicles
- Security standards compliance
- Cloud offerings (SaaS, PaaS, IaaS) risk assessment
- Supplier risk assessment
Why Do You Need Automotive Cybersecurity?
Increased connectivity of autonomous vehicles brings more potential security risks.
Like any other device connected to a network, an SDV can become a target of various cyber-attacks, from ransomware to vehicle theft.
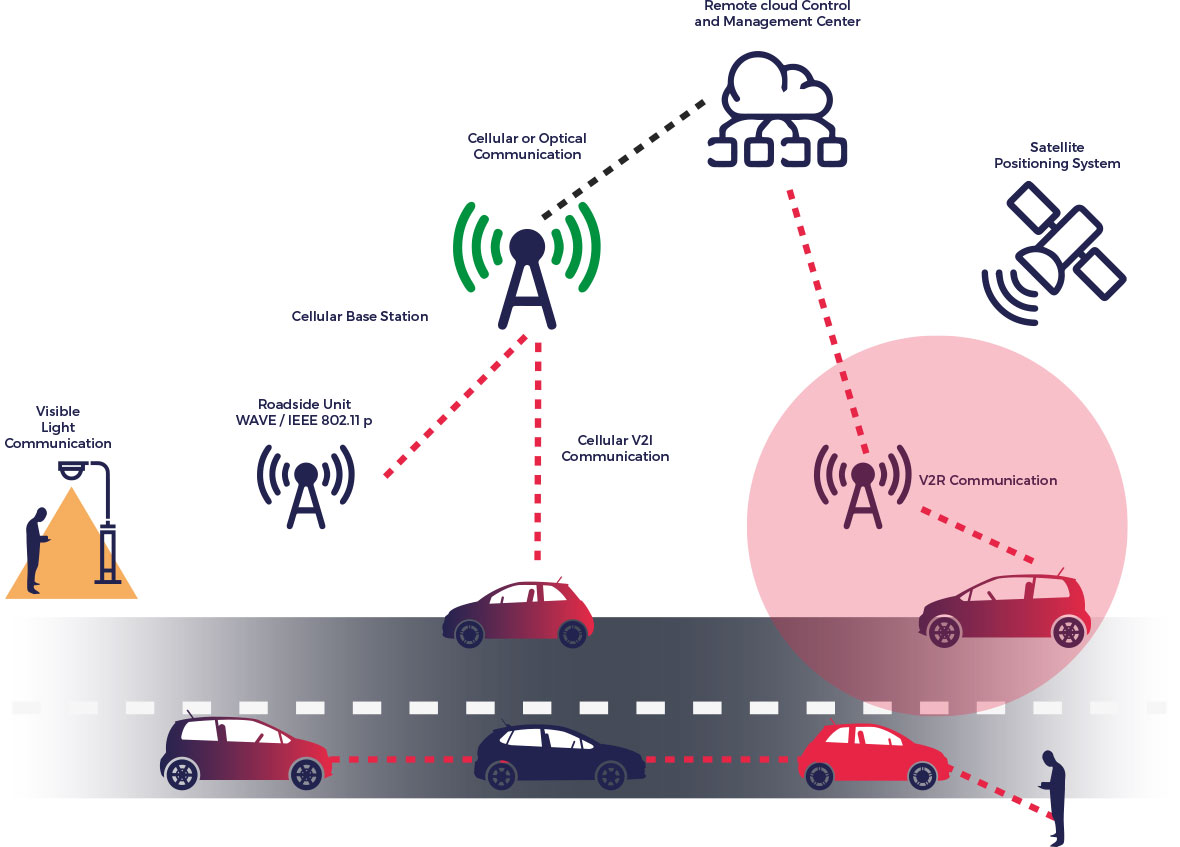
Autonomous Vehicles Communication Systems
- WiFi networks
- Roadside computing units
- Vehicular cloud services
- Dedicated short-range communications (DSRC)
- Vehicle-to-vehicle (V2V)
- Vehicle-to-infrastructure (V2I)
- Vehicle-to-everything (V2X)
Why Choose NOVELIC for Automotive Cybersecurity Consulting
Through years of working on challenging projects, we have learned the ins and outs of automotive software and hardware and potential weak points of each system. Major automotive OEMs and Tier 1 clients have trusted us with their products.
Software-Defined Vehicles
(SDV) Cyber Threats
Common typers of cyber attacks:
- Man-in-the-middle (MitM) attack
- Side-channel
- 3rd party taking control of the vehicle/surrounding infrastructure
- Denial-of-service (DoS)
- Unauthorized software modifications
- 3rd party accessing PII (personally identifiable information)
Automotive Cybersecurity Risk Assessment Methodology
There is currently no internationally recognized cyber security standard/framework for autonomous vehicles, which is why applying best practices and security controls is essential. We conduct risk assessment using the information assurance methodology based on the following:
- Automotive SPICE for Cybersecurity
- ISO/IEC 33020:2015
- ISO 27005:2013
- ISO/IEC 27005:2011
- Information technology
- Security techniques
- Information security risk management

Image source: ismsalliance.com
Supplier Risk Assessment
Supplier Risk Assessment Checks We Offer:
Supplier Security Technical Testing
Internal penetration testing, internal application vulnerability testing, internal build reviews, independent penetration and application vulnerability testing
Information Security Management System (ISMS)
Assessing main ISMS components: IS roles, IS budget, IS policy, staff screening, security training&awareness, access control, cryptography
ISO 27001:2013 Independent Annual Compliance Review
Establishing whether the supplier has undertaken formal certification against ISO 27001: 2013
Basic Supplier Checks
Validating company history, main business activity, staff recruitment process, use of third parties, reputational standing and client reviews, history of any data breaches/security incidents
PCI-DSS Compliance
Checking if the supplier holds attestation in any respect to the Payment Card Industry Data Security Standard (PCI DSS)
Supplier Physical Site Security
Site location, site ownership, site security, site accreditation
Supplier Cloud Offerings
(SaaS, PaaS, IaaS) Risk Assessment
Cloud Offerings Risk Assessment We Offer:
Data in transit protection
Ensuring data transiting networks are adequately protected against tampering and eavesdropping via a combination of network protection and encryption
Asset protection and resilience
Ensuring the data and the assets storing or processing it are protected against physical tampering, loss, damage, or seizure
Personnel Security
Ensuring provider staff is subject to personnel security screening and security education for their role
Clients separation
Ensuring separation exists between different clients of the service to prevent one malicious or compromised consumer from affecting the service or data of another
Supply Chain Security
Ensuring the service provider’s supply chain satisfactorily supports all of the security principles that the service claims to implement
Identity and Authentication
Ensuring access to all service interfaces (for consumers and providers) is constrained to authenticated and authorized individuals